Latest Articles
Read our Medium publications on cybersecurity topics

Finding Password Reset Vulnerabilities
Learn how to identify and exploit common password reset vulnerabilities in web applications.
Read on Medium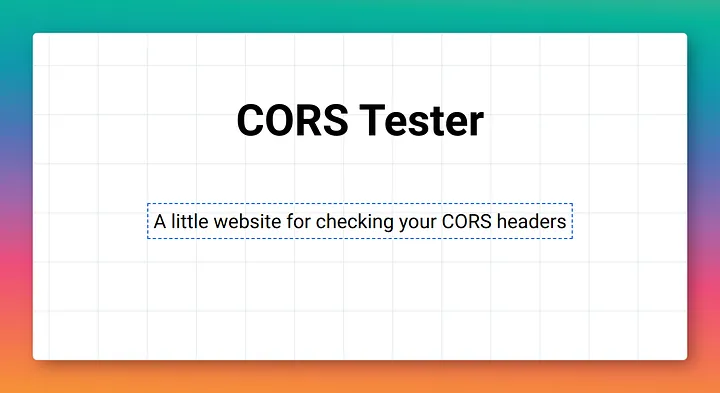
CORS Checker: Your Ultimate Testing Tool
Discover our powerful tool for testing Cross-Origin Resource Sharing configurations and vulnerabilities.
Read on Medium
Mastering Bug Bounty: Strategies for Success
Proven strategies and techniques to maximize your success in bug bounty programs.
Read on Medium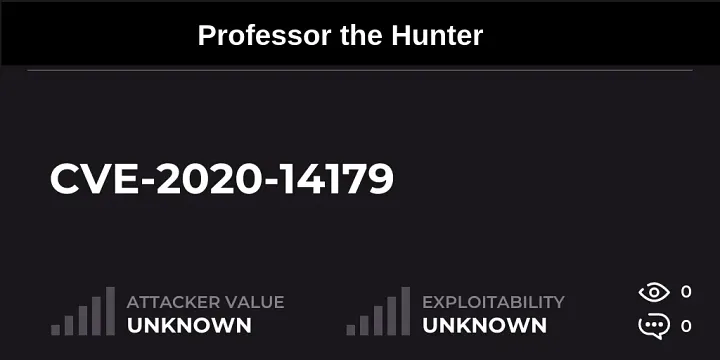
CVE-2020-14179: Jira Information Disclosure
Technical analysis of an unauthenticated information disclosure vulnerability in Atlassian Jira.
Read on Medium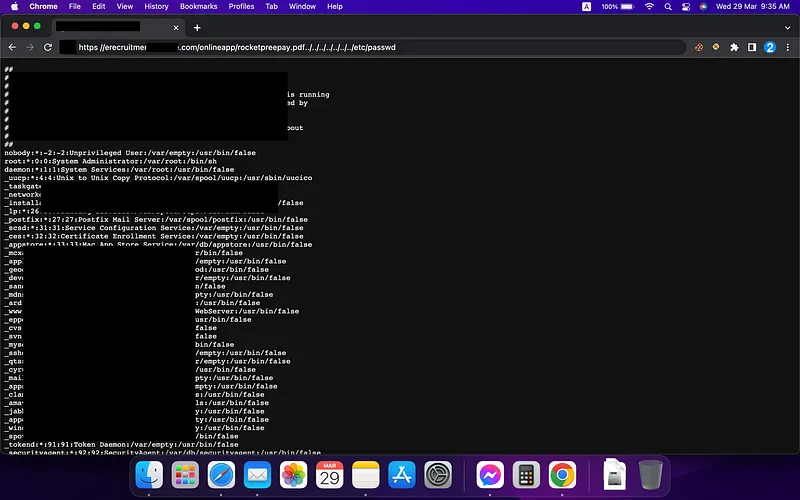
LFI Vulnerability Exploited in Edge Network
A case study of discovering and exploiting a Local File Inclusion vulnerability in a major network.
Read on Medium
Epic Games Open Redirect Bypass: $500 Bounty
How I discovered and reported an open redirect vulnerability in Epic Games that earned my first bounty.
Read on Medium